Download HijackThis Fork Free 2025 for Windows PC
Download HijackThis Fork Free 2025 for Windows PC
Comprehensive Guide to HijackThis Fork
In the ever-evolving landscape of cybersecurity, having reliable tools to maintain system integrity is essential. Among these tools, HijackThis Fork stands out as a notable application designed to help users identify and rectify unwanted software and potential security threats. As users increasingly rely on digital platforms for work and communication, the need for effective system maintenance solutions has never been more critical.
This article will explore the various aspects, including its features, installation process, and overall effectiveness in maintaining system health. By the end, you will have a thorough understanding of how this tool can help protect your digital environment.
What is HijackThis Fork?
It is an enhanced version of the original tool, which was developed to assist users in identifying and removing potentially harmful software from their computers. Building on the foundation laid by its predecessor, this version incorporates new features and improvements aimed at enhancing user experience and effectiveness in malware detection. The tool is particularly valuable for those who seek to maintain their systems without relying solely on automated antivirus solutions.

Key Functionalities
The primary function of HijackThis Fork is to provide users with a comprehensive scan of their system to identify malicious items, browser hijackers, and other unwanted software. It does this by thoroughly analyzing critical areas, such as startup items, browser extensions, and system configurations. The detailed reports generated by the tool empower users to make informed decisions about which items to remove or keep. This level of transparency is crucial for users who want to maintain control over their system’s security without relying entirely on automated processes.
Installation and Setup
Downloading the Software
Installing is a straightforward process, making it accessible to users of all technical backgrounds. Users can easily download the software from its official website or reputable software repositories. The download size is minimal, which means it doesn’t take long to obtain, even on slower internet connections.
Step-by-Step Installation
- Run the Installer: After downloading, double-click the installer file to initiate the setup process. This will launch the installation wizard, which guides users through the necessary steps.
- Follow the Prompts: Carefully read the license agreement and accept the terms to proceed. This ensures that users understand their rights and responsibilities when using the software.
- Choose Installation Location: Users have the option to select their desired installation directory or accept the default location. This flexibility allows for better organization based on user preferences.
- Complete Installation: Click the “Finish” button to complete the installation process. Once installed, users can launch the application immediately and begin using its features.
Initial Configuration
Upon installation, configuring HijackThis Fork to suit individual preferences is highly recommended. Users can adjust various settings, such as scan frequency and reporting options, to tailor the tool’s functionality to their specific needs. This customization ensures that the tool operates optimally and aligns with the user’s approach to system maintenance.
Features
It is loaded with features that enhance its usability and effectiveness. Here are some of the most significant functionalities:
Comprehensive Scanning
One of the standout capabilities is its comprehensive scanning process. The tool thoroughly examines various components of the system, including:
- Startup Items: Identifying programs that automatically launch during boot-up, which can often include unwanted software.
- Browser Extensions: Reviewing installed add-ons in web browsers, which are common targets for malware.
- Hosts File: Checking for suspicious entries that could redirect web traffic, a common tactic used by malicious software to control users’ browsing experiences.
This level of scrutiny is invaluable for users who want to ensure that their systems remain free from unwanted and potentially harmful software.
Detailed Reports
Following a scan, generates in-depth reports that provide users with a clear breakdown of detected items. These reports categorize findings, helping users understand potential threats better. The categorization includes designations such as “safe,” “suspicious,” or “malicious,” which aids users in making informed decisions about what to keep or remove. This transparency is crucial, especially for those who may not have advanced technical knowledge but still wish to maintain their system’s security.
User-Friendly Interface
Designed with usability in mind, the interface of HijackThis Fork is intuitive and straightforward. Users can navigate through the application with ease, accessing various features without needing extensive technical knowledge. This focus on user experience is particularly important, as it allows individuals of all skill levels to leverage the tool effectively. Clear menus and organized layouts contribute to a seamless experience, enabling users to focus on maintaining their systems rather than struggling with complicated interfaces.
Quarantine Functionality
To enhance safety further, includes a quarantine feature that allows users to isolate suspicious items before deciding to remove them permanently. This precautionary measure ensures that critical system components are not inadvertently deleted, which can lead to further complications. By quarantining items, users can evaluate their impact on system performance and security without committing to immediate deletion. This feature is particularly valuable for those new to malware removal, as it provides a safety net during the decision-making process.
Community Support and Database
Benefits from a community-driven database that provides users with insights into the items detected during scans. This collaborative effort helps identify new threats and enhances the tool’s overall effectiveness. Engaging with the community allows users to stay informed about emerging malware trends and share their experiences, resulting in a more robust understanding of system security. The collective knowledge of users and experts contributes to a continuously evolving tool that adapts to the changing landscape of cybersecurity threats.
Customer Support and Help Center
Available Resources
For users needing assistance, HijackThis Fork offers a variety of support resources to ensure a smooth experience. These resources include:
- User Manuals: Comprehensive guides that explain how to use the tool effectively, covering all features and functionalities.
- FAQs: A dedicated section addressing common questions and troubleshooting tips, which can be particularly helpful for new users.
- Forums: Community forums where users can share experiences, ask questions, and receive advice from fellow users and experts in the field.
These resources empower users to resolve issues independently while fostering a supportive community environment.
Contact Support
If challenges persist that remain unresolved through available resources, users can contact support via email or through the official website. The support team is typically responsive and can provide personalized assistance, ensuring that users can rely on expert help when needed. This level of customer support is crucial for maintaining user confidence in the tool’s effectiveness and reliability.
Pricing and Plans
Available at no cost, making it accessible to a wide range of users, regardless of their financial situation. This lack of a price tag allows individuals to focus on system maintenance without worrying about subscription fees or hidden costs.
Comparison with Paid Tools
While some users may consider premium tools for added features, HijackThis Fork offers sufficient functionality for most casual users. Many established security applications require a subscription for ongoing updates and support, while providing an effective solution for users who prefer a straightforward, no-cost approach. This makes it an attractive option for those who may not have the budget for premium security software but still want to maintain a clean and secure system.
Pros and Cons
Pros
- Free to Use: The application is accessible to anyone without financial commitment, making it an excellent choice for budget-conscious users.
- Effective Scanning: Provides thorough checks for malware and unwanted software, helping users maintain system integrity.
- User-Friendly: The easy-to-navigate interface allows users of all skill levels to utilize the tool effectively, promoting broader usage and understanding.
- Community Support: Access to forums and shared knowledge enhances the user experience and provides valuable insights into system maintenance.
Cons
- No Real-Time Protection: Unlike some paid tools, it does not offer continuous monitoring, which may leave systems vulnerable between scans.
- Requires User Input: Users need to interpret scan results and make decisions on what to remove, which might be challenging for beginners without technical experience. This aspect can lead to accidental deletions if users are not careful.
User Experiences and Testimonials
Positive Feedback
Many users have reported overwhelmingly positive experiences with HijackThis Fork. Testimonials frequently highlight the tool’s effectiveness in identifying and removing malware that other programs often overlook. Users appreciate the clarity of reports, which break down findings into understandable categories, making it easier to take appropriate action. Furthermore, the accessibility of the tool, combined with its free nature, has made it a popular choice for individuals looking to enhance their system security without incurring costs.
Areas for Improvement
However, some users have noted that the application could benefit from enhanced documentation and more intuitive navigation for beginners. A more robust tutorial section could help new users feel more confident in using the tool effectively. Additionally, while the community forums are a great resource, the presence of more official support channels could further enhance user satisfaction and provide quicker resolutions to common issues.
Comparison with Other Tools
When compared with other similar tools, several distinctions emerge. Many established security applications offer real-time protection but come with a price tag. In contrast, focuses on manual scanning and user-driven decision-making, making it a valuable asset for users who prefer to actively manage their system’s security.
Alternatives
- Malwarebytes: This well-known application offers comprehensive real-time protection but requires a subscription for full functionality. It is often used alongside other tools for layered security.
- AdwCleaner: A free tool that specializes in removing adware but lacks the broader scanning capabilities of HijackThis Fork. It is useful for specific tasks but may not provide the same level of overall system analysis.
Choosing the Right Tool
Ultimately, the choice between these tools depends on user needs. For those seeking a straightforward, no-cost option for periodic scans, is an excellent choice. Conversely, users requiring constant protection may prefer a premium solution that offers real-time monitoring and automated threat responses.
Tips for Using HijackThis Fork
Best Practices
To maximize effectiveness, users should consider the following tips:
- Regular Scans: Schedule periodic scans to ensure ongoing system health. Regular use helps catch potential threats before they can cause significant problems.
- Review Reports Carefully: Take the time to understand the scan results and research unfamiliar items. This practice is essential to making informed decisions about what to remove.
- Use Quarantine Wisely: Always quarantine suspicious items before deletion to avoid accidental loss of essential files. This step provides a safety net and allows for further evaluation of potential threats.
Staying Informed
Stay updated on the latest threats and software updates to ensure that it remains effective. Engaging with community forums can also provide insights into emerging issues and solutions. By participating in discussions, users can learn from others’ experiences and gain valuable knowledge about system security.
Frequently Asked Questions (FAQs)
What is HijackThis Fork used for?
Primarily used to scan and identify malware, adware, and other unwanted software on a computer, providing users with detailed reports to make informed decisions about system maintenance.
Is it Fork free?
Yes, it is completely free to use, making it accessible to a wide range of users.
Can I use HijackThis Fork on multiple devices?
Yes, users can install and use on multiple devices, provided they download the application for each one.
Does HijackThis Fork provide real-time protection?
No, it does not offer real-time protection. It is designed for manual scans and user-driven actions.
Importance of System Maintenance
Regular system maintenance is crucial for optimal performance and security. Applications like HijackThis Fork play a vital role in identifying and removing unwanted software that can slow down systems or pose security risks. This proactive approach to system health ensures that computers run efficiently and remain secure against emerging threats.
Benefits of Regular Maintenance
- Enhanced Performance: Regular scans help keep systems running smoothly by removing unnecessary files and applications. This can significantly improve boot times and overall responsiveness.
- Increased Security: Identifying and eliminating malware reduces the risk of data breaches and other security incidents. Regular maintenance acts as a preventative measure against potential threats.
- Prolonged Lifespan: Keeping systems clean and optimized can extend the overall lifespan of hardware. By avoiding the buildup of unwanted software, users can ensure that their devices remain functional for longer periods.
Tutorials and Additional Resources
To further assist users, numerous tutorials and resources are available online. These can provide guidance on using HijackThis Fork effectively, as well as tips for general system maintenance.
Video Tutorials
Many users find video tutorials helpful for visual learning. Platforms like YouTube host a variety of guides that demonstrate how to use the tool step-by-step, illustrating its features and functionalities in real-time.
Community Forums
Engaging in community forums can also be beneficial. Users can share experiences, ask questions, and learn from others who have faced similar challenges. These forums often serve as a repository of collective knowledge, where users can find solutions to specific issues and gain insights into best practices.
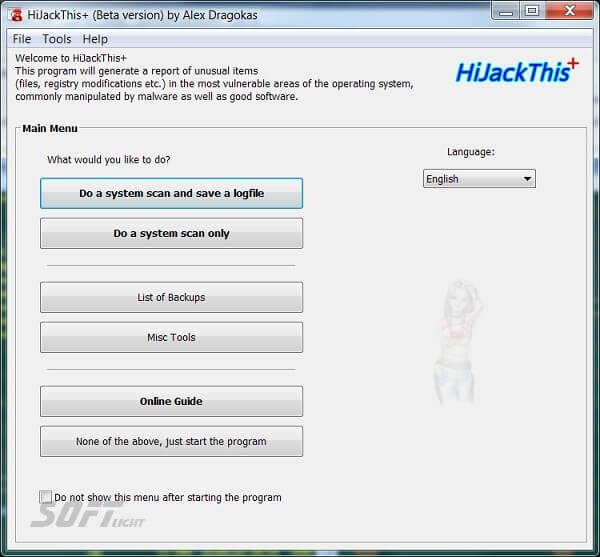
System Requirements
Before installing HijackThis Fork, it’s essential to ensure that your system meets the requirements. Here are the basic requirements:
- Operating System: Compatible with Windows versions, including Windows 7, 8, 10, and later. This widespread compatibility ensures that most users can take advantage of the tool.
- RAM: A minimum of 2 GB is recommended for optimal performance. This ensures that the application runs smoothly without affecting overall system performance.
- Disk Space: At least 50 MB of free space for installation and operation. This requirement is relatively low, making it easy for users to accommodate the software.
Conclusion
In conclusion, HijackThis Fork serves as a powerful tool for users looking to maintain their system’s health by identifying and removing unwanted software. With its user-friendly interface, comprehensive scanning capabilities, and supportive community resources, it empowers users to take control of their system maintenance. While it may not provide real-time protection, the affordability and effectiveness make it a valuable addition to any cybersecurity toolkit.
By regularly utilizing this tool and staying informed about system maintenance best practices, users can enhance their overall computing experience and safeguard their devices against potential threats. As technology continues to evolve, proactive tools like HijackThis Fork will remain essential for ensuring that systems operate smoothly and securely in an increasingly digital world.
Technical Details
- Category: Antivirus
Software Name: HijackThis
- Licence: Open Source
- Version: Latest
- File size: 7 MB
- Kernel: 32/64-bit
- Operating Systems: Windows, and more
- Languages: multiangular
- Developed by: Stanislav Polshyn
- Official website: HijackThis
Download HijackThis Fork Free 2025